Introduction
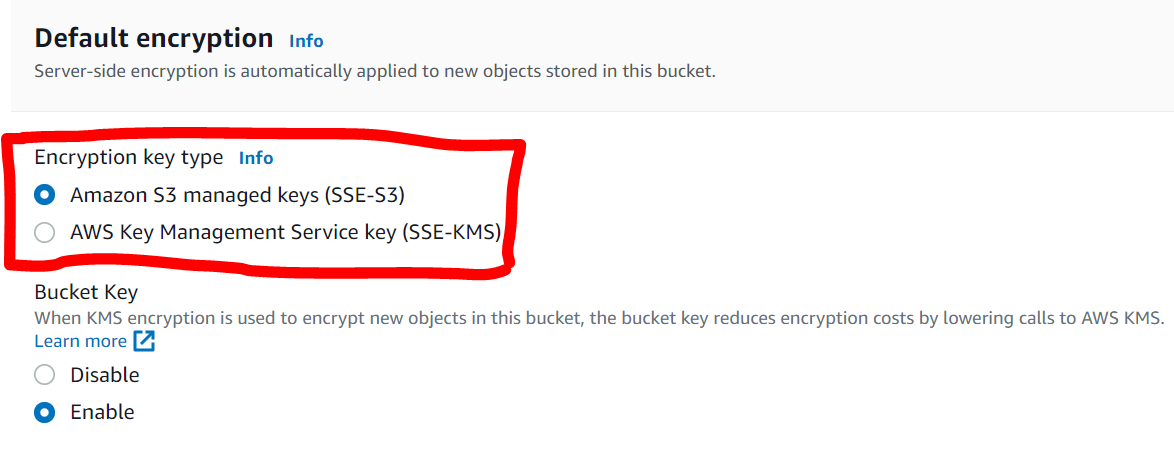
Cloud Computing escalates the security risks of an organization. This happens because of the extended trust boundary associated with deploying IT assets beyond the data centers of the asset owners. The trust boundary exposes organizations to such risks as internal malicious actors, man-in-the-middle attacks, ransomware attacks, and more. In order to mitigate these risks, cybersecurity experts have come up with frameworks to address cloud security – risks related to unauthorized access and risks related to the data breach.
In this article, we shall discuss a three data-oriented security mechanisms developed by cloud service providers and give examples of how