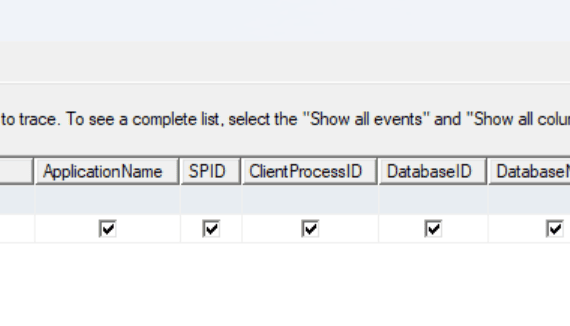
SQL Server Row Level Security Deep Dive. Part 6 ...
As seen in the previous section, there are several ways bad actors can attempt to bypass RLS. […]

As seen in the previous section, there are several ways bad actors can attempt to bypass RLS. […]
As mentioned in previous sections, RLS is an addition to security and should not be used as […]
One of the primary reasons to implement RLS is to facilitate reporting and ease the administrative burden. […]
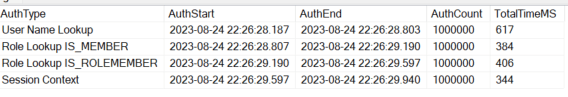
Previous sections gave a brief introduction to RLS, including some common use cases. They also showed how […]
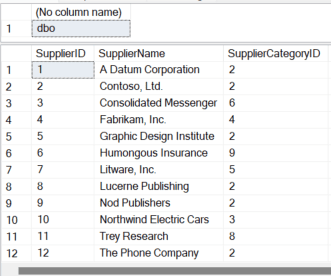
The previous section in this series was an introduction to Row Level Security (RLS) and some use […]