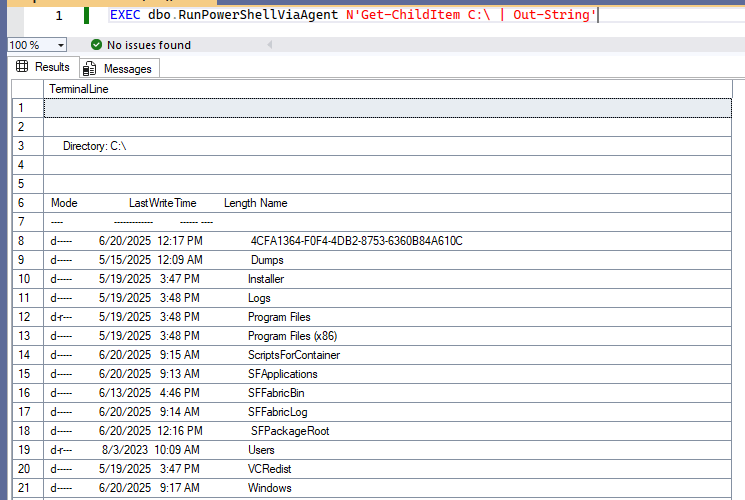
In Part 1, I explored how to bend SQL Server Agent to our will and peek under the hood of Azure SQL Managed Instance (SQL MI), gaining full OS access to the container (all without relying on xp_cmdshell). But once I realized what kind of door I’d opened, curiosity pushed us further, tempting us to try even bolder tricks.
What if I could sneak an entire binary file into our SQL MI container and execute it natively?
For our tests, nothing fancy, just a Sysinternals diagnostic tool, but imagine the possibilities this could unlock for more advanced experimentation. But experimentation